Social Engineering, concrete examples and how to defend yourself
In the previous post, we introduced the concept of social engineering, exploring how this technique organizes itself, studies its victims, and attacks them. We concluded that the best defense strategy is knowledge. In this new article, we will put these resources into practice to identify social engineering attacks and protect ourselves most effectively.
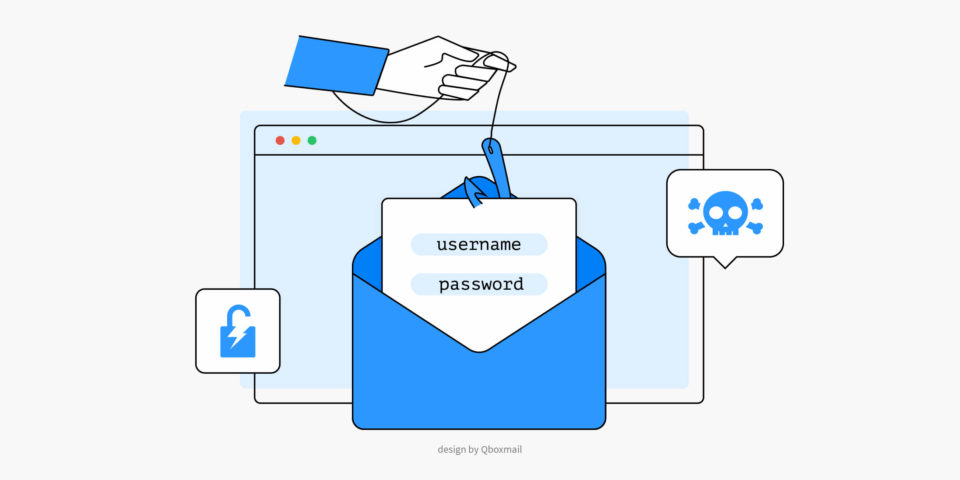
Email Phishing
A phishing attack involves the sending of counterfeit emails that appear to come from legitimate financial institutions, companies, or online services. Users are manipulated into clicking on malicious links or sharing personal information, such as passwords or credit card numbers. An example? An email that appears to be from your bank, asking you to click the link below to “update” your account password.
Social Engineering via phone
The target receives a call with a spoofed phone number that appears to come from a legitimate entity but is actually used to obtain sensitive information or perform actions such as transferring funds to other accounts. The fraudster calls the victim from the forged number, presenting himself as the victim’s new bank representative, always maintaining a calm, polite and professional demeanour. He convinces the victim that his bank account will be closed and that he must transfer his savings to another account by means of a wire transfer.
Cyberattacks on social network
Attackers can study people’s profiles on social media such as Facebook or LinkedIn for months, collecting personal information that can be used to create personalised messages, increasing the credibility of attacks. For example, an attacker might send an email to the victim quoting personal details taken from their social media profiles and then extort ransom demands and threats.
Tech support scams
In this type of scam, a caller claims to be the computer support technician and informs the victim of an imaginary problem on the computer. The aim is to convince the victim to grant access to his or her computer or to pay for the ‘resolution’ of the problem.
Password attacks
Attackers can exploit the weakness of passwords by trying to induce people to share them voluntarily. How? By phoning or emailing, claiming that a ‘password reset’ is necessary for security reasons and requesting the current password.
Financial scams with long-distance love deception
The criminal creates a fake profile on social networks, with interesting information and attractive photos. He makes contact with his victim, uses romantic, flattering language, pretends to be romantically interested to the point of establishing a virtual relationship of ‘love and trust’. At a certain point, a situation of danger and urgent financial need emerges, so the criminal asks the lover for ‘help’, exploiting the target’s emotions and feelings.
Identity theft
Identity theft involves the fraudulent use of an individual’s personal information, such as name, residence and financial data. Granting this data leads to the real risk of opening bank accounts, purchasing goods or services, creating fake companies or documents, and carrying out online crimes, all in your name, unknowingly. With social engineering, the attacker gains access to these highly personal data, simply by inviting you to grant them, by means of implication and manipulation.
Always remember that any transfer, action or password granted as a result of a social engineering attack does not guarantee any kind of reimbursement, not even through a lawsuit. Obtaining justice can be extremely difficult, because it is you who deliberately clicked on that link or sent that money, prompted by the attackers’ deception.
The consequences of a social engineering attack can be very serious, but prevention is the best shield. Trust must be given with extreme caution, and education is your best weapon against these threats.
Online security is a shared responsibility, and investing in education and awareness is an act of prevention that can protect not only you, but also those around you and your business.
Awareness is the key word in reducing risk, information is power and sharing knowledge is the basis for creating a safer online environment for all.