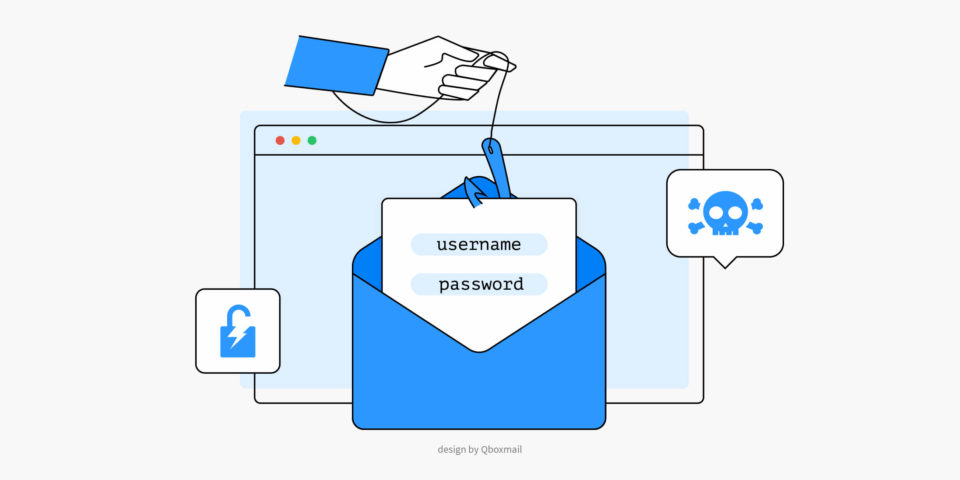
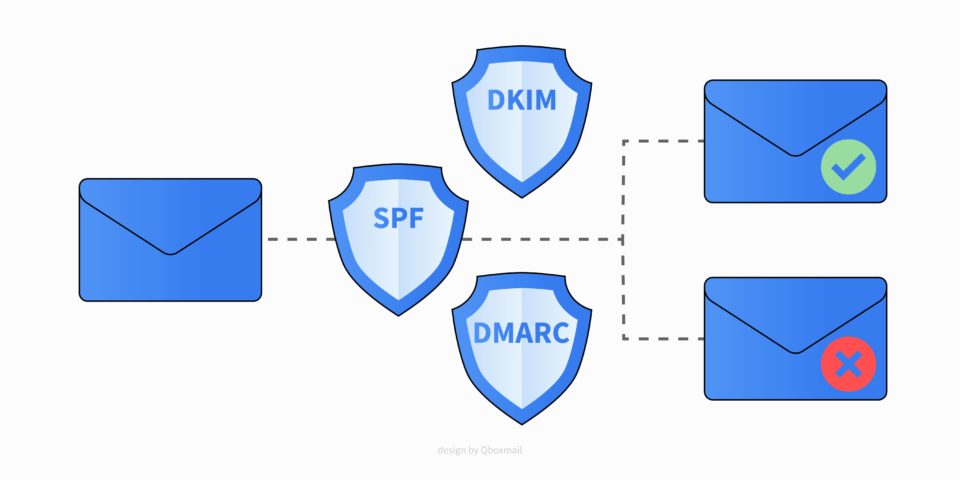
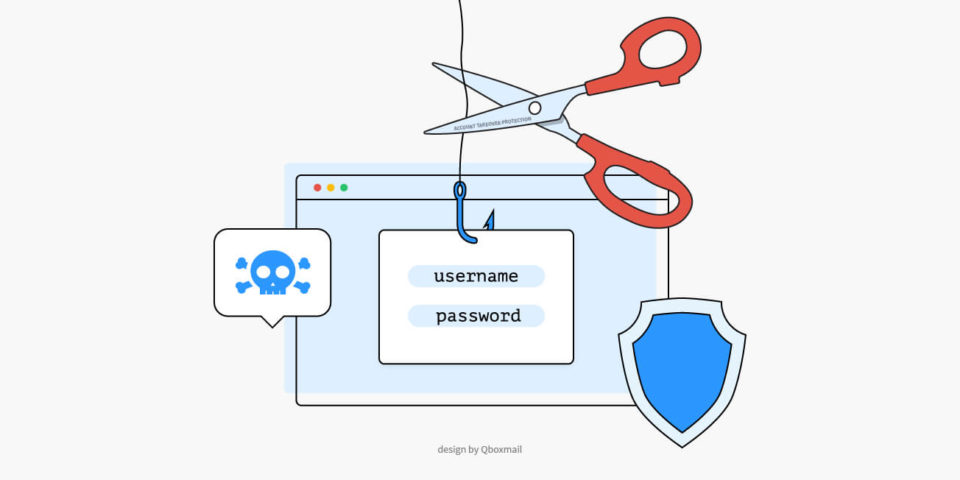
Social Engineering, the cyber attack exploiting human weakness
Social engineering is a cunning technique that exploits human weaknesses to carry out attacks and obtain sensitive information for fraudulent purposes. There is no antivirus that can fully protect you from this threat. This technique relies on manipulating people through...