What is Account Takeover and how to protect corporate emails against cyberattacks
Account Takeover is a type of cyberattack used to embody a victim’s identity by stealing their Webmail login credentials.
Identity theft is often used to send spam emails under the victim’s name. However, it could also be used to carry out more complex scams — e.g. scammers might be able to change the IBAN on an invoice so to receive a transfer on their bank account instead of the victim’s.
How does it work?
Kinds of cyberattacks like the Account Takeover have been around for several years. The attacker’s goal is to get hold of the virtual identity of one or more victims, to exploit them himself or sell them to others. To do this, hackers aim to steal or guess a victim’s password to access their email accounts.
Password theft can happen in several way. The most used are:
- Infection of the victim’s computer/smartphone with Trojan;
- Guessing the password with brute-force attacks launched by botnets;
- Being provided the credentials directly by the user through Phishing;
- Using already stolen passwords from previous attacks on other platforms, hoping that the victim is using them on different services;
- Studying the “target” —victim of the attack— on social media networks or through other public sources to extract data that could be forming a password.
The first types of attacks aim at automatically recovering a large number of credentials at once to resell them on the dark web to other scammers. These could also launch new attacks —e.g. by sending phishing emails to retrieve further new credentials.
How about when the victim is studied? This is potentially the most dangerous kind of attack. It aims to get hold of a user’s credentials when he or she may have access to money management in their organization. The aim is at diverting wire transfers to the scammers’ bank accounts. This is how the “fake CEO scam” developed.
How to defend yourself
Defending yourself against this types of scam requires you to consider two main aspects.
Human factor
People working for or collaborating with a company must train in order to know the risks associated with these scams and recognize suspicious signs. A typical “fake CEO scam” scenario would involve an email from the ‘CEO’ asking you for an urgent bank transfer and inviting you not to disturb him for further clarification because he is playing golf.
Company employees must know that it is always good to be suspicious of strange requests arriving via email, even if they seem to come from trusted people.
In addition, users should understand the importance of proper password management by avoiding passwords that are too simple or reusing one password on multiple services.
Technological factor
The company must adopt the most appropriate and up-to-date security measures. This is the most efficient way to help protect their employees email accounts. Generally, any access to administrative panels should involve adequate security measures, such as two-factor authentication, or restricted access from trusted IP addresses.
Workstations and smartphones must be protected by adequate anti-virus security systems. Furthermore, the company network must also be protected by a Next Generation Firewall —i.e. a firewall that not only is opening and closing ports, but is also analyzing network traffic to intercept potential risks when users browse the web or read emails.
The more measures and security levels are implemented (both procedural and technical), the more difficult it is for scammers to carry out cyberattack against your company.
A big responsibility is on the external digital providers that the company relies on for web hosting, for instance, and similar services. Service providers must equip themselves with adequate security measures and protection against any type of scams. In fact, in some cases, the attack takes place outside the company perimeter and cannot be detected in any way by the company security systems except, when it has already caused damage. Make sure to ask questions about cybersecurity, when looking for a new service provider.
How the Qboxmail Account Takeover Protection works
The Qboxmail cloud business email management service already includes an Account Takeover Protection system.
Protection consists of various levels of analysis and procedures. Access to Webmail is constantly monitored. If the system detects anything abnormal, due to the time or origin of sent/received mail, it can trigger an alarm. In addition, certain types of actions are also monitored and can trigger alarms, such as attaching suspicious material to an email or abnormal sending volumes.
The user is also notified when someone sets a forwarding address, directing mail to an external address. This is another type of setting hackers use to silently spy on a victim’s mail.
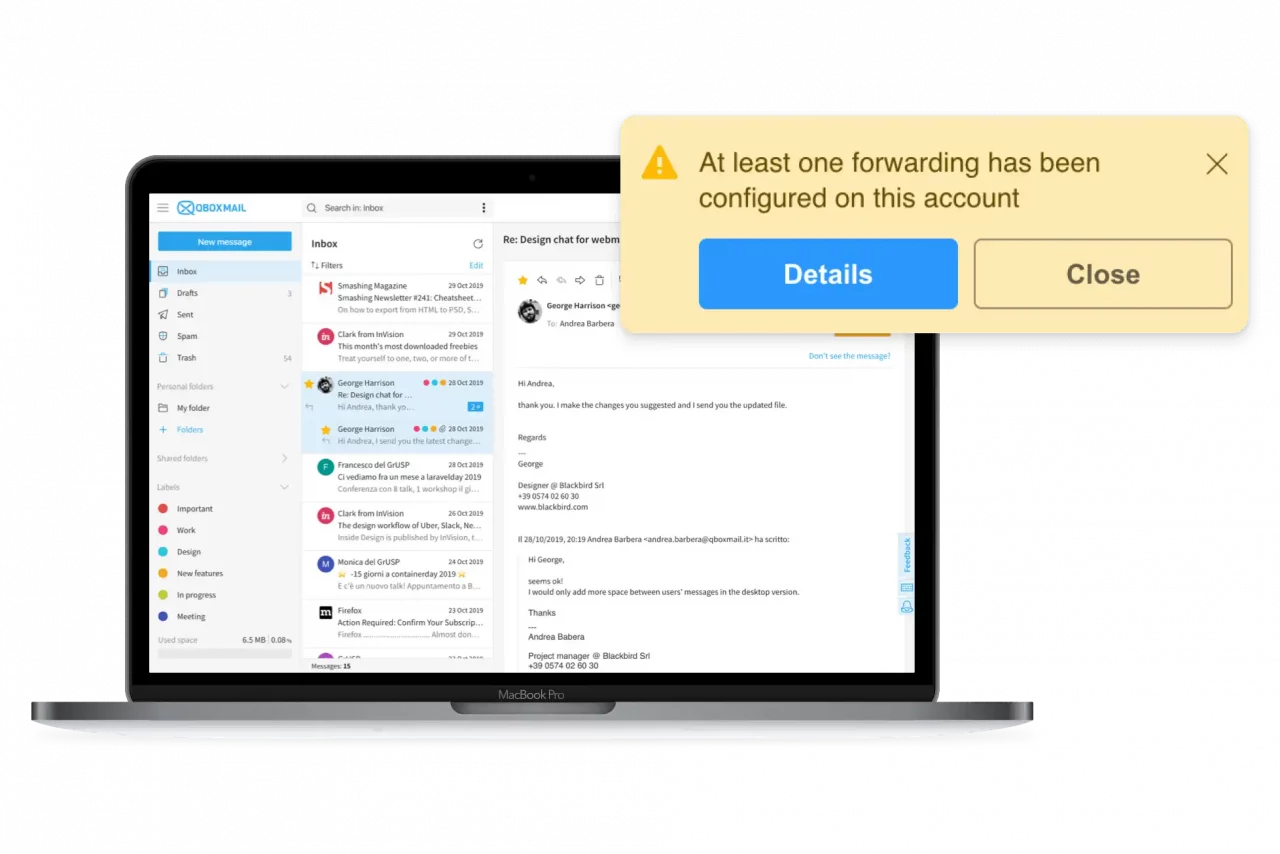
When a suspicious activity is identified, the system automatically notifies both the user and his or her manager, while the anomalous activity is immediately inhibited.
Through the Qboxmail control panel, it is possible to analyze these suspicious activities through ETlive, our system of analysis of email traffic logs in real-time. From here, it is also possible to apply additional security measures, such as two-factor authentication; blocking reuse of old passwords; restricting access to email accounts through trusted IP addresses or corporate VPNs.