Protect your emails against cyberattacks
What about Account Takeover?
Account Takeover is a cyberattack in which an attacker assumes a victim’s identity by stealing their webmail login credentials. Attackers often use this stolen identity to send spam under the victim’s name. They can also carry out more complex scams—for example, changing the IBAN on an invoice so that a payment lands in the scammer’s account instead of the victim’s.
How does it work?
Attackers have relied on Account Takeover techniques for years. Their goal is to seize one or more users’ virtual identities, then exploit or sell them. To achieve this, they must obtain or guess victims’ passwords. Common methods include:
- Infecting the victim’s computer or smartphone with a Trojan
- Launching brute-force attacks via botnets to guess passwords
- Phishing users into revealing their credentials directly
- Using credentials stolen in previous breaches, hoping users recycle passwords
- Researching targets on social networks or public sources to discover password clues
Mass credential-theft attacks focus on harvesting large lists of passwords to resell on the dark web. Those buyers can then launch fresh phishing campaigns to steal even more credentials.
When attackers research a specific target, the threat escalates. They aim for users with financial authority and then divert wire transfers into scammer accounts. This tactic underlies the so-called “fake CEO scam.”aunch new attacks —e.g. by sending phishing emails to retrieve further new credentials.
How to defend your business
Defending against Account Takeover requires action on two fronts.
Human factor
Employees and collaborators must train to recognize these scams. In a typical fake CEO scenario, they receive an urgent email from the “CEO” requesting a wire transfer and advising against follow-up questions because “he is in a meeting.”
Users should always:
- Question unexpected requests for urgent transfers, even if they appear to come from senior staff
- Use unique, strong passwords and never reuse them across services
- Hover over links to verify URLs before clicking, or type addresses manually if in doubt
A well-trained employee can thwart most phishing attempts before they succeed.
Technological factor
The company must adopt the most appropriate and up-to-date security measures. This is the most efficient way to help protect their employees email accounts. Generally, any access to administrative panels should involve adequate security measures, such as two-factor authentication, or restricted access from trusted IP addresses.
Workstations and smartphones must be protected by adequate anti-virus security systems. Furthermore, the company network must also be protected by a Next Generation Firewall —i.e. a firewall that not only is opening and closing ports, but is also analyzing network traffic to intercept potential risks when users browse the web or read emails.
The more measures and security levels are implemented (both procedural and technical), the more difficult it is for scammers to carry out cyberattack against your company.
A big responsibility is on the external digital providers that the company relies on for web hosting, for instance, and similar services. Service providers must equip themselves with adequate security measures and protection against any type of scams. In fact, in some cases, the attack takes place outside the company perimeter and cannot be detected in any way by the company security systems except, when it has already caused damage. Make sure to ask questions about cybersecurity, when looking for a new service provider.
How the Qboxmail Account Takeover Protection works
Companies must implement robust, up-to-date security measures to protect email accounts:
- Two-factor authentication (2FA): Require app-based or hardware-token second factors rather than SMS alone.
- IP restrictions: Limit access to webmail and administrative panels to approved IP ranges or corporate VPNs.
- Behavioral monitoring: Track login locations, email volumes, and changes such as new forwarding rules to spot anomalies.
- Endpoint and network protection: Keep antivirus and endpoint detection on all devices, and deploy a next-generation firewall that inspects encrypted traffic.
The more layers you add, the harder you make it for attackers to succeed.
External service providers also share responsibility. Hosting or email vendors must enforce strong security—attacks that originate outside your perimeter often bypass your internal defenses until they inflict damage. Always ask potential providers about their cybersecurity measures before signing a contract.
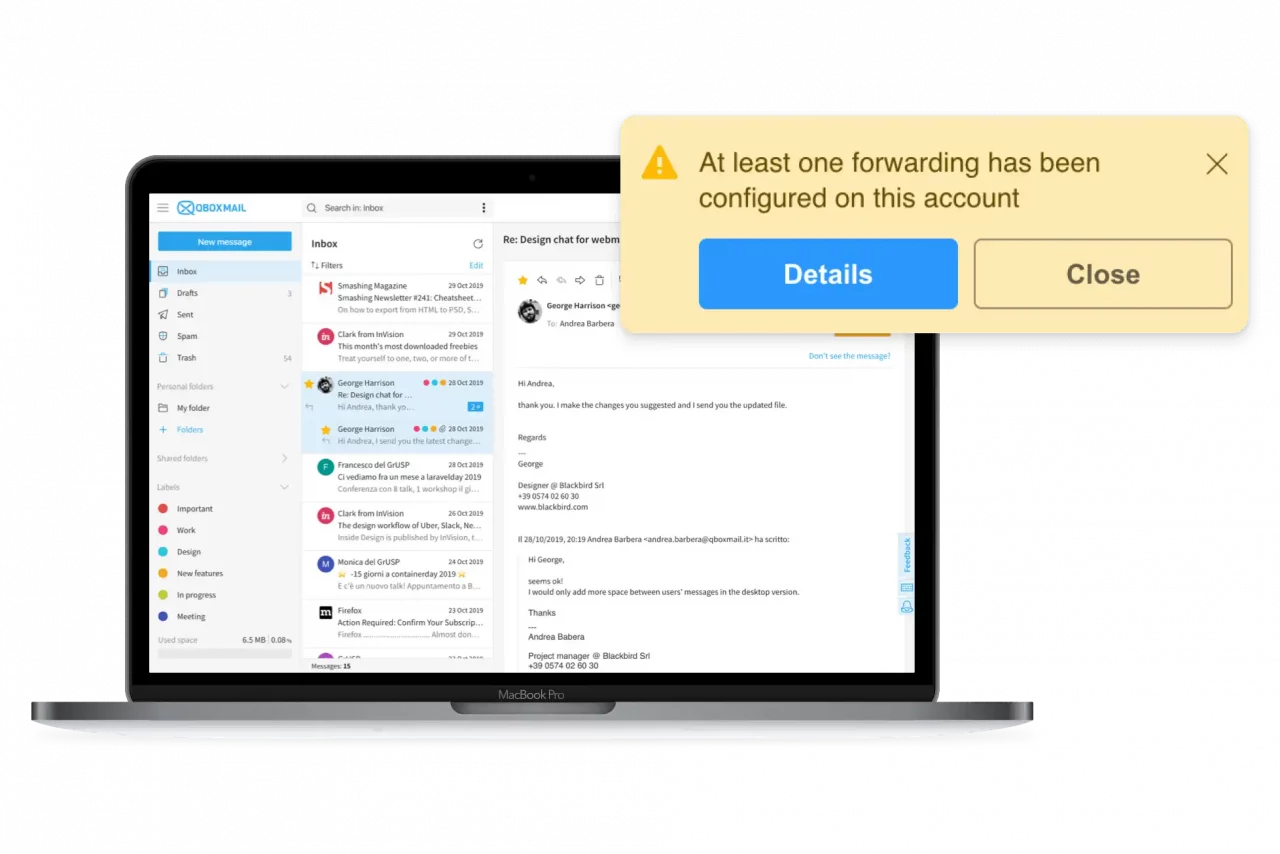
How the Qboxmail Account Takeover Protection works
Qboxmail’s cloud email platform includes built-in Account Takeover Protection:
- Continuous monitoring: We analyze webmail access in real time for unusual times or geolocations.
- Action-based alerts: The system flags suspicious behaviors such as setting up unknown forwarding addresses or sending volume spikes.
- Immediate notifications: Both the user and their manager receive alerts when the system detects anomalies, and the suspicious action is automatically blocked.
- ETlive dashboard: Through our control panel, administrators can review live traffic logs and enforce extra security policies—forcing 2FA, blocking password reuse, or restricting access to trusted IPs or VPN connections.
By combining human vigilance with these technical defenses, Qboxmail ensures your corporate emails stay safe from Account Takeover attacks.