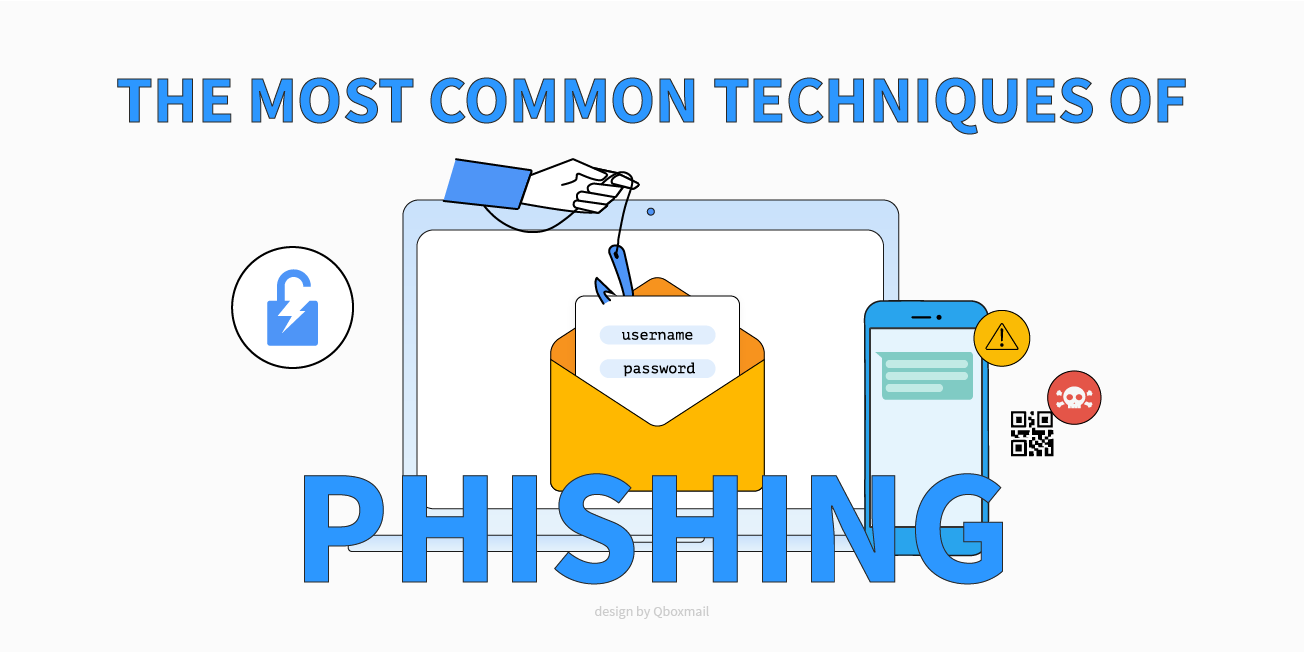
The Most Common Phishing Techniques in 2025
The most common phishing techniques: stolen emails, stolen passwords and cybersecurity risks
Learn how to defend yourself from the different types of phishing attacks.
Phishing is evolving fast and becoming harder to detect. Today it uses everyday channels like email, SMS and phone calls, and it now integrates AI and deepfakes.
For companies, MSPs and IT professionals—but also for non-technical users—understanding how these attacks work is key to protecting data, people and communications.
In this article we introduce the most common and advanced phishing techniques. We will cover them one by one in the next posts with practical examples and defense strategies.
Phishing: the most common and advanced techniques to watch out for
Quishing: QR Code scams
Quishing relies on fake QR codes that lead to fraudulent websites or install malware. It’s particularly dangerous because the link remains hidden until the user scans the code.
Vishing: phone call attacks
With Vishing, criminals call pretending to be from banks or IT departments. Using social engineering and spoofed caller IDs, they obtain confidential data or convince victims to approve unauthorized operations.
Smishing: SMS fraud
SMS is still a popular channel for scams. With a few words and alarmist messages, attackers push users to click on fraudulent links, often related to fake shipments or fake bank alerts.
AI-powered Spear Phishing
Spear Phishing has existed for years, but AI makes it far more convincing. Personalized emails and messages tailored to the recipient make it hard to tell the difference from legitimate communication.
Deepfakes and social engineering
AI-generated video and audio are the latest evolution. Fake executives can request wire transfers or approvals, exploiting the trust employees place in familiar voices and faces.
Why do these techniques work?
These scams succeed because they use channels we deal with every day. Email, SMS and phone calls feel familiar and safe, which makes people lower their guard.
Psychological pressure is another factor. Urgency, stress and fear of missing out drive quick reactions, often without the necessary checks. This mechanism can affect anyone, including ICT professionals used to managing complex situations.
Reduce the risks today
Phishing is one of the most common cyberattack vectors. It can cause severe data loss, exposure of sensitive information and reputational damage.
Training employees helps them recognize suspicious messages and protect the entire organization. Training also raises awareness of social engineering risks and the manipulation tactics used by cybercriminals.
Some best practices apply in every scenario:
- Be wary of links received via email or SMS.
- Always verify financial requests or changes of bank details through a second channel.
- Train and regularly update your staff.
Stay tuned: in the next articles we will analyze each phishing technique in detail and share practical defense measures.
In the meantime, discover how Qboxmail supports companies and resellers with secure, always up-to-date solutions against new threats.